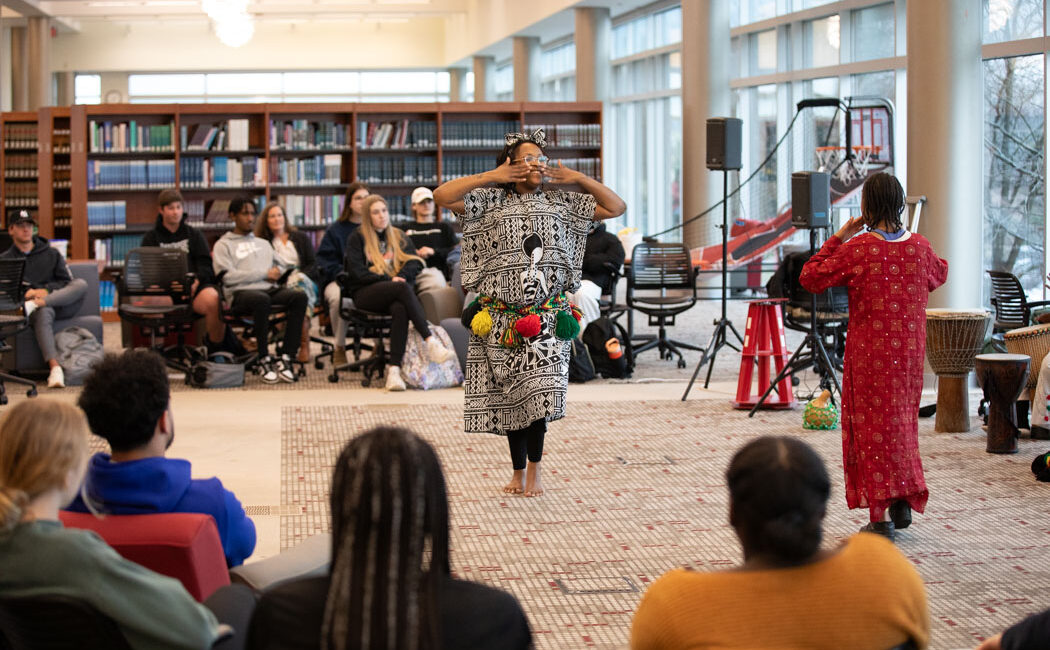Featured Stories
Recent Stories
Davenport Commencement honors graduates and Mary Free Bed CEO
Davenport University will honor 1,300 graduates at its commencement ceremony on Sunday, April 28, 2024. The ceremony will be held […]
Davenport University introduces only cancer registry certificate program in Michigan
The American Cancer Society estimates that there will be nearly 65,000 newly diagnosed cases in Michigan this year, and slightly […]
Nursing shortage triggers changes, Davenport University responds with flexibility
Nationwide, there’s a shortage of healthcare professionals, and that need is expected to grow. Davenport University is addressing the talent […]
Davenport University launches one-of-a-kind bilingual program
Davenport University hosted a news conference on its Grand Rapids W.A. Lettinga Campus March 5, 2024, to officially launch Casa […]
A Message from the President
As seen in the Spring DU Review Magazine Davenport University has built a solid reputation for being agile, for responding […]
Davenport student overcomes incredible odds to earn her degree
Seira Jenkins is a first-generation, non-traditional student at Davenport University who was forced to put her dream of attending college […]
Davenport Nursing – it’s all in the family
Pictured left to right: Dawn Overbeek, Veronica Overbeek, Elizabeth Overbeek-Buresh and Melinda Overbeek-Conklin. Sometimes sisters don’t like to be followed […]
Davenport alum transitions from player to coach
When Veronica Overbeek, BSN ’19 first stepped foot on Davenport’s Lettinga Campus as a freshman in 2015, she quickly realized […]
The evolution of the Panthers
Davenport University’s athletic program has evolved over time to become a force to be reckoned with. Over the years, numerous […]
Internships prepare students for their chosen careers
Most college students entering the final phase of their educational journey are focused on finishing classes, graduating, and landing the […]
Accounting and Finance Forum connects students with industry experts
Educators at Davenport University take every opportunity to connect students with industry experts to expand upon what is being taught […]
West Michigan Jewels of Africa bring Pan-African culture to Davenport
The West Michigan Jewels of Africa (WMJA) brought the sights and sounds of a traditional African village to Davenport University’s […]
Women’s History Month inspires us to move forward
A message from Davenport University president Richard J. Pappas March is Women’s History Month. It has been so since 1987 […]
Davenport University launches groundbreaking bilingual degrees program
Leaders at Davenport University announced a groundbreaking initiative that leads to bilingual degrees with professional proficiency in English and Spanish. […]